Mac vulnerability is very rare, but it really does occur. When you're afraid if your computer is infected by it and you want your Mac to have a reliable protection tool, you arrive at the right spot. Here's how to have a quick virus search to look for Trojan malware onto your computer, what to do to get cleaned of Mac bugs for good, as well as how to stop being compromised instead.
Removing Trojan from Mac is possible. If you're seriously concerned that there is some kind of virus and malware or even superbug onto your Mac, we're here just to assist you to find out what is going on and, if needed, tidy up the problems-all provided for free. A number of the sources that offer guidance on Mac malware protection are businesses that are seeking to market virus ideas that help certain suggestions highly selective, however now you can get advice and guidance.
We're going to discuss removing Trojan from Mac and keep out of every other malware that may be hiding. We'll also clarify why it would be possibly not really a virus because of Apple's tight macOS security, however, if it is, we'll help you learn about both the free and inexpensive solutions that will defend your computer from threats.
Part 1. Can You Get Trojan Virus on Mac?
It has been said that Apple devices don't really have viruses or malware. Although this is completely accurate for other iOS-based devices, including the iPhone or iPad, that's not actually completely correct for Macs today. There have been several significant malicious code incidents in past years, but a major distinction relative to Microsoft Windows would be that there will never be a Mac malicious outbreak. In addition, since the launch of OS X (presently identified as macOS), a small percentage of the overall amount of Macs has been compromised.
There are some causes why Mac strains wouldn't want to seize control of the virus. Which is the tight security designed through macOS, the second is the way that this is incredibly difficult for malware to 'propagate' itself or expand to another Mac. Yet Macs still come into the spotlight for anti-virus software developers. There are indeed a lot of hateful users who still see Macs-and their customers-as main candidates, so in this guide, we explain what to do to stay secure and stop or to get rid of the vulnerabilities and malware they're trying to throw onto your computer. (We also suggest that you review our latest Mac protection tips and our compilation of the best Mac antivirus software, which we suggest as our preferred choice.)
Notice that to some point we're going to connect and balance the words malware and virus, but they're really different definitions. The malware appears to have taken the type of applications that claim to do some task, but instead do more illegal, like stealing information. Viruses are tiny, discreet blocks of software that somehow go onto the device and thus are planned to be hidden. There are some other forms of attacks, including such malware as well as other malicious software schemes, in which an effort is made to gain information that can be used to get funds from anyone. Removing Trojan from Mac how to do it easily and efficiently read down below.
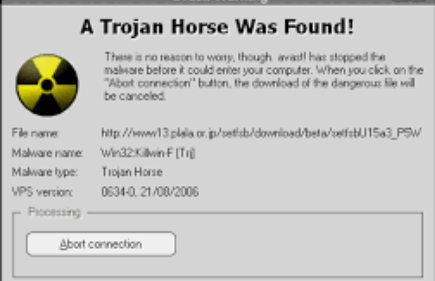
How to Detect Trojan Virus on Mac?
Common Trojan viruses could perhaps cause serious damage to several consumers and firms. It's a good thing to know the possible symptoms of prevalent Trojan viruses. Popular Trojan viruses conduct the following malicious attacks on your device after you have been diagnosed: How to detect if your computer is infected with the Trojan virus.
1. Pop-ups and Strange Messages
You will notice that your device shows you only some various types of pop-ups as well as notifications? It really doesn't matter if it was an advertising campaign or a statement that says your computer is damaged. You could then be sure that you are beginning to feel symptoms of familiar Trojan viruses. You could have had a fraudulent antivirus and malware onto your device.
2. Very Sluggish Systems
When you feel that creating so many documents and operating several programs simultaneously will slow down your machine, this wasn't the only explanation. The common Trojan virus signs could also affect the slowness of your device since it may be consuming several resources.
3. Delayed Communication to the Online Platform
Another of the typical signs of Trojan viruses is the sluggish Network. You might not have been able to communicate to it several times either. If you recognize that anyone else in the room or workplace will interact, be informed. This is one of the most typical symptoms of Trojan viruses. If you are compromised, the Trojan Horse Virus may link to the URL and create different communications cycles. This limits the usable bandwidth or renders it difficult to connect to the internet.
4. Inaccessible Programs
An application that you'd need is not running at all since mild corrective maintenance needs to become one of the typical signs of Trojan viruses. A few other schemes may work, and some of your programs did not work. To really be sure, you should just go to check with all your security features as well as the process.
5. A Malicious Screen
Are there any unnecessary screens and search engines that exhibit posts? This is a positive indication of a specific Trojan virus effect. Inappropriate redirecting congestion to some other manipulative website. This will trick you into using a fraudulent webpage that you probably wouldn't notice at all.
6. Note Disturbing Signs
These are some of the most disturbing signs of the Trojan horse virus. Your critical missing files could have been exploited by a Trojan virus. The Trojan horse will erase or encrypt content, or transfer your information to some other location. You should really be concerned once this sort of stuff occurs to you.
7. Disabled Virus Protection and Firewall
It's not just data that would disappear in your device, the virus protection, and firewall features can indeed be shut off throughout the common Trojan viruses effects. This leaves the Machine much more prone to cyber threats. There is already a significant computer security problem and that you should respond quickly to that as well.
These are the common symptoms of how you will know when your device is infected with the Trojan virus.
Part 2. How to Remove A Trojan Virus from Mac?
Removing Trojan from Mac how to prevent it? As for most forms of malware, most Trojans could be found using a typical anti-virus and anti-malware software. That being said, maintaining the Mac device up-to-date is possibly the even more critical precaution against Trojan Horse contamination. It's not really a negative idea for Google's "Mac Trojans" every once in a while, to see whether there would be any forms of Trojans that have been actually creating difficulties for a bunch of Mac users. Even though Trojans were already comparatively and blissfully rare on Macs, almost all of the larger Trojan software that really can damage OS X would be published to big technology media. Keeping up with the cyber-attacks out there will lead to a greater understanding of your web activity and more informed of any suspicious signs that your Machine can experience.
When removing Trojan from Mac you should use this if you're searching for a fast way to prevent the Trojan virus from Mac:
- Just go to the Safari Preferences section (or whatever other Mac browser).
- Try searching on the Homepage category. Make absolutely sure the homepage is the one you're looking for.
- Go to the Extensions section now.
- Check for any extension that could have been linked to the Trojan virus from Mac pop-ups.
- Delete whatever extension that could be behind the Trojan virus for computer
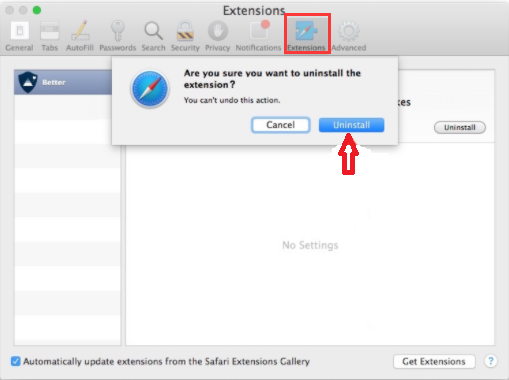
If you'd like to get control of the Trojan virus on your Mac or Removing Trojan from Mac, take the following steps:
- Activate your Safari tab now. From the list connect Safari browser.
- Select on Preferences. For the next screen choose Extensions.
- Check for some newly added extensions that could have been the cause for the Trojan virus onto computer pop-ups.
- Select the Uninstall key beside the extension you wish to delete.
The purpose of a potential risk like Mac Trojan could even oftentimes be quite unexpected. Such an advanced part of malware has been intended to perform major illegal activities. This might effectively erase the information from the computer device, change your program configurations, initiate any malicious operations, or illegally inject certain horrible viruses. It's frightening to think of that as well, but without any time, your computer will be packed with horrific malicious software such as Malware, Spyware or even Rootkits and so on, due to the ability of a sole Trojan horse, which will build malicious software and bugs to safeguard your device.
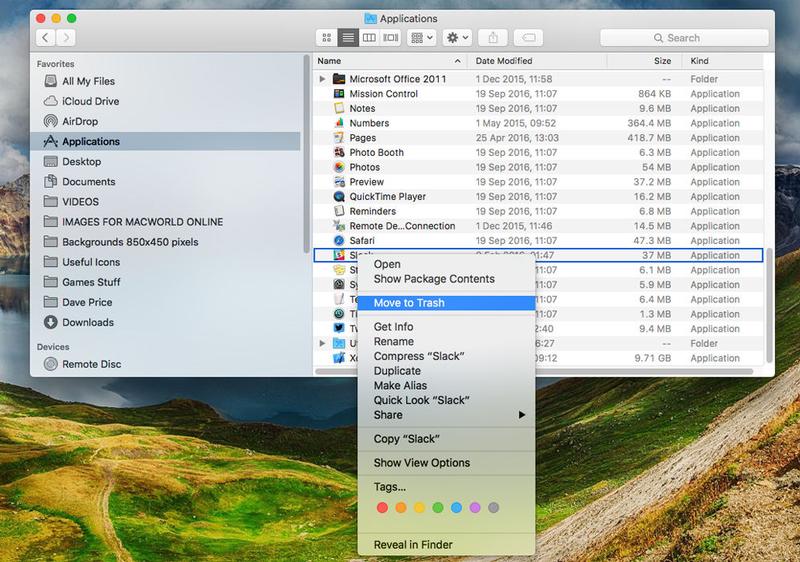
You could even try this simple guide to start the deletion of a Trojan from Mac:
- Within the OS X, select "Go" mostly in the top left corner of your screen.
- Go to Applications.
- In the Applications directory, search for something unusual that could be behind the alerts of the Trojan Mac.
- Right-click on items like this and pick Move to Trash to start deleting the Trojan computer.
There could be several forms of internet transmission that could be utilized of a virus including Mac Trojan. It's indeed usually extremely difficult to detect a concealed Trojan infection without any of the help of specific virus protection.
Otherwise, you might easily have ended up with a terrible virus like this on your Machine without even getting an idea about all this. The Trojan could have been disguised as a normal email or file, a file, a connection, an advertisement, a friend's post, or perhaps an enticing online deal. This is why, literally, it wasn't enough to try to prevent such stuff, since you may meet potential providers of Trojan vulnerabilities on a regular basis. Of course, you must keep away from specifically questionable and sparse web locations.
Protect Your Mac from Virus
Ask some Mac users about Mac's antivirus, and that they will inform you that the macOS doesn't even get viruses, and there is no need to think about all this. That's really not exactly real, sadly. Although no significant outbreak or plague of Mac malware has occurred in the wild, macOS has also been affected by malware a number of times. Just lately, Meltdown including Spectre malware has abused vulnerabilities in intel processors and damaged Mac.
To protect your Mac from vulnerabilities you need to have the most and reliable anti-malware program which will give the exact protection to your device. One of these is the PowerMyMac Application tool which you can use to protect your computer's privacy, it has the exact privacy feature that will safeguard the important information of your device.
It even acts as a cleaner, a filter that declutters what's underneath your Mac, and privacy clears up your browsers where you do much of your operation. I think this among the most important uses of an application cleaner because it can prevent you from getting malware attacks.
Removing Trojan from Mac using the PowerMyMac application tool. Follow all the steps below to easily protect your Mac from these kinds of viruses.
- Download and install the PowerMyMac application tool from the official website of the application.
- Launch and open the application onto your device.
- Then select and click the Privacy feature of the application.
- Click on SCAN then have a view of them.
- Choose the browser you need to clean or select all to clean everything.
- Click on the CLEAN button right of the page.
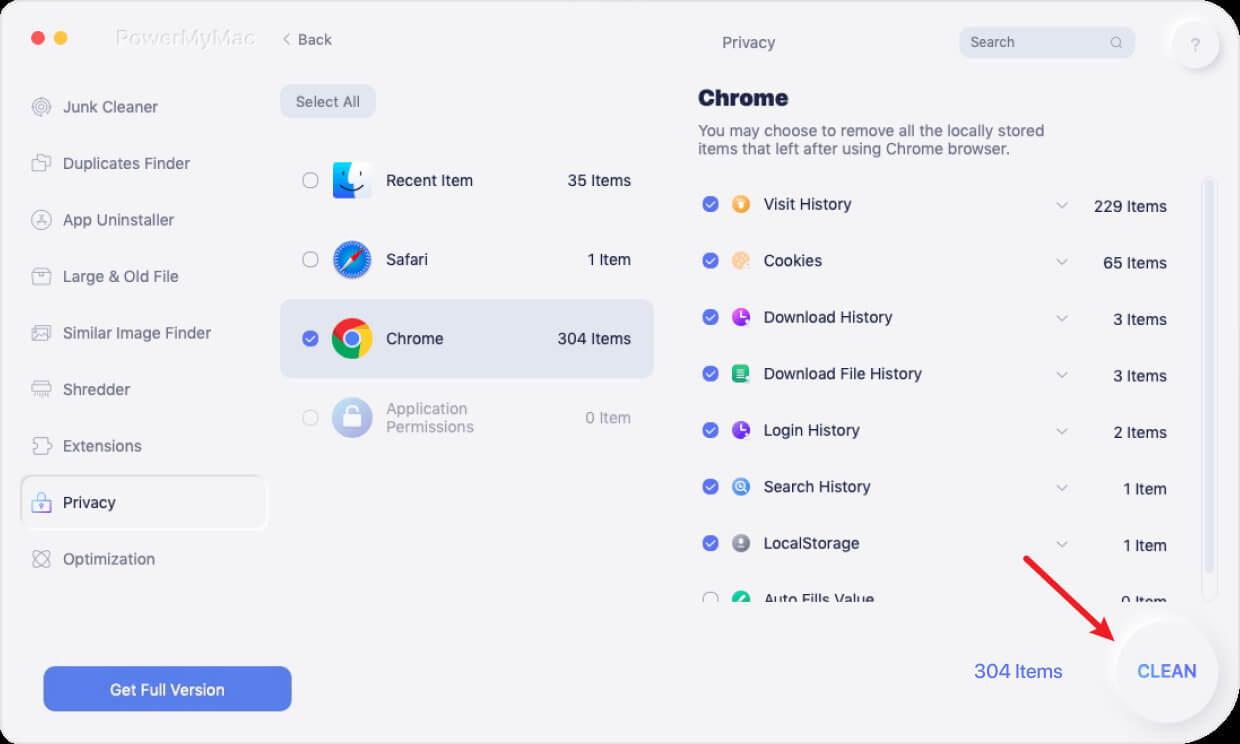
If you already have one or even more browsers that you're using, you might also need to repeat the procedure by choosing the next browser.
Part 3. Free Trojan Virus Removal Tools
Removing Trojan from Mac Using these free tools.
AVG Antivirus Free
The major reason for using AVG AntiVirus Free: Thousands believe it to secure them, it consistently outperforms top rankings among all the best antivirus production in the market, and it provides you several of the strongest safety features around for free. The vital antivirus launches in just a few seconds, and afterward prevents you permanently-without slowing you down. With AVG AntiVirus FREE on your side, you are covered on multiple sheets.
Avast's Finest Trojan Scanner and Cleaner
Visible Trojans will damage your information and slow down your computer (and some other computers as well). Trojans are packaged as harmless data, but begin causing problems once they get into your device. Fortunately, Avast does have the fastest and most reliable Trojan scanner also in the market. There's literally no easier way to uninstall ASAP Trojans.
Bitdefender Antivirus Free Version
It is an efficient, discreet form. This anti-malware app does not really ask the questions when you download it. It's all silent about finding and deleting something that poses a serious threat to your safety and protection. It detects applications that act inappropriately, checks web links to recognize fraud, and also has advanced malware and spyware detection that can spot vulnerabilities that no one has ever seen before. And as well as, the target customers a reboot test each time you launch your computer.
Ad-free, and even hassle-free, Bitdefender Antivirus Free Version is a wonderful software that works easily and quietly when you're getting on with something a little more important. Its extensive set of tools to secure your computer makes Bitdefender the great cheap anti-malware program that you can use nowadays. It's all the security you want from a handy bundle.
Avira Free Security Suite
Avira Free security suite is one of the most advanced free security solutions found on the website. There are also encrypted searching and securing individual solutions, as well as a device optimizer to boost up the computer, which is usually paid for the packages. If this is not sufficient, there is also a free VPN included within up to 500 MB per month, and also a password manager and a privacy options administrator.
SpyBot Search and Destroy
Is a pioneer of the malware battles, going all the way back to the very first adware in 2000, and although it doesn't search against viruses it's in the Home edition, which is about £ 10, AU$20 free program does a good job of detecting and repairing malicious software, malware, and spyware. It was more of a maintenance tasks tool than just a system security tool, though, and you will need to be vigilant when you get it: there are false models in existence intended to inflict harm, not address it.
Part 4. Conclusion
It's not really difficult to confirm if your computer was infected or not, since these days malicious hackers are able to spend a lot of time shielding their program and manipulating what their applications are doing on an infected machine. It is very challenging to include a description of the typical signs of an infected device even though the same effects could also be triggered by hardware compatibility issues or device failure, so here are only a few suggestions that may indicate that your computer was already infected.